Difference between revisions of "Timing Channel Mitigations for RISC-V Cores"
From iis-projects
(Created page with "==Introduction== [timing_channels_intel.png|right|These two ''timing channel matrices'' of a Haswell class Intel processor show the conditional probability of observing an out...") |
|||
| (9 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
==Introduction== | ==Introduction== | ||
| − | |||
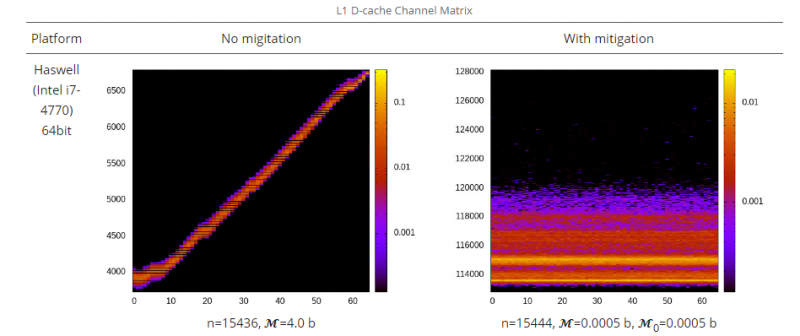
| + | [[File:Timing channels intel.png|thumb|800px|These two ''timing channel matrices'' of a Haswell class Intel processor show the conditional probability of observing an output symbol (vertical axis) given an input symbol (horizontal axis). The effect of timing mitigation techniques can be clearly observed in the right matrix, where almost no correlation can be observed anymore. Images taken from [http://ts.data61.csiro.au/projects/TS/timingchannels/arch-mitigation.pml].]] | ||
| + | |||
| + | The Spectre and Meltdown vulnerabilities that publicly surfaced about a year ago did not only severely impact companies and cloud service providers, but also shook our trust in the computing systems we use on a daily basis, such as our laptops and mobile phones [masters2018]. These vulnerabilities are essentially a combination of speculative execution techniques present in today's processors, combined with shared hardware state and timing channels that make it possible to leak information. | ||
| + | |||
| + | Timing channels are among the remaining unsolved problems in secure hardware architecture design, and it is argued that '''security needs a new hardware-software contract''' [Ge2018a], [Ge2018b]. Security is and has always been the operating system's (OS) job. For instance, memory protection is already well established - '''but the OS must also enforce time protection'''. In order to enforce time protection, additional hardware support for state flushing is required. | ||
| + | |||
| + | In this project, we will investigate how such ''hardware knobs'' can be added to the Ariane 64bit RISC-V processor and come up with a proof-of-concept implementation. Insights gained during this process shall be fed back to the RISC-V community in order to guide the design of future secure RISC-V systems. | ||
==Project description== | ==Project description== | ||
| − | The purpose of this project is to | + | The purpose of this project is to enhance the Ariane RISC-V processor [arianeGit] with additional hardware mechanisms to flush the state of various functional and non-functional units in the pipeline. Specifically, we need to be able to erase state from |
| − | * | + | * functional units, |
| − | * | + | * instruction frontend, |
| − | * | + | * translation look-aside buffer (TLBs), |
| + | * branch predictor(s), | ||
| + | * instruction and data caches | ||
| − | in | + | in an effective way and with predictable or even constant latency [Ge2018a]. These ''knobs'' are then exposed to an OS that implements the mitigation techniques outlined in [Ge2018b]. |
| − | + | Your task will be to carry out and test the required hardware mechanisms both in simulation and on a FPGA mapping of the Ariane processor. Further, the power, area and timing impact of the implemented mechanisms shall be assessed by mapping the core to a modern ASIC technology. | |
| + | |||
| + | Depending on the project progress, initial experiments with the seL4 microkernel [seL4] can be carried out in collaboration with University of South Wales (UNSW). | ||
==Required Skills== | ==Required Skills== | ||
To work on this project, you will need: | To work on this project, you will need: | ||
| − | * to have worked in the past with at least one RTL language (SystemVerilog or Verilog or VHDL) -- having followed the VLSI1 / VLSI2 courses is | + | * to have worked in the past with at least one RTL language (SystemVerilog or Verilog or VHDL) -- having followed the VLSI1 / VLSI2 courses is mandatory |
* to have prior knowledge of hardware design and computer architecture -- having followed the "Advanced System-on-Chip Design" or "Energy-Efficient Parallel Computing Systems for Data Analytics" course is recommended | * to have prior knowledge of hardware design and computer architecture -- having followed the "Advanced System-on-Chip Design" or "Energy-Efficient Parallel Computing Systems for Data Analytics" course is recommended | ||
| Line 24: | Line 34: | ||
* familiarity with basic system security principles | * familiarity with basic system security principles | ||
| − | ===Status: | + | ===Status: In Progress=== |
| − | + | : Supervision: [[:User:Zarubaf|Florian Zaruba]], [[:User:Scmoritz|Moritz Schneider]] | |
| − | : Supervision: | ||
===Professors=== | ===Professors=== | ||
| Line 33: | Line 42: | ||
==Practical Details== | ==Practical Details== | ||
| − | |||
| − | |||
===Meetings & Presentations=== | ===Meetings & Presentations=== | ||
| Line 49: | Line 56: | ||
==Resources== | ==Resources== | ||
| + | * [masters2018] Jon Masters, Red Hat Inc. "Exploiting modern microarchitectures: Meltdown, Spectre, and other attacks" [https://people.redhat.com/jcm/talks/FOSDEM_2018.pdf] | ||
* [arianeGit] Ariane is a 6-stage, single issue, in-order CPU which implements the 64-bit RISC-V instruction set [https://github.com/pulp-platform/ariane] | * [arianeGit] Ariane is a 6-stage, single issue, in-order CPU which implements the 64-bit RISC-V instruction set [https://github.com/pulp-platform/ariane] | ||
* [Zaruba2018] Zaruba, Florian "Ariane: An open-source 64-bit RISC-V Application-Class Processor and latest Improvements" [https://content.riscv.org/wp-content/uploads/2018/05/14.15-14.40-FlorianZaruba_riscv_workshop-1.pdf] | * [Zaruba2018] Zaruba, Florian "Ariane: An open-source 64-bit RISC-V Application-Class Processor and latest Improvements" [https://content.riscv.org/wp-content/uploads/2018/05/14.15-14.40-FlorianZaruba_riscv_workshop-1.pdf] | ||
| Line 54: | Line 62: | ||
* [Ge2018a] Ge, Qian et al. "No Security Without Time Protection: We Need a New Hardware-Software Contract." [https://ts.data61.csiro.au/publications/csiro_full_text//Ge_YH_18.pdf] | * [Ge2018a] Ge, Qian et al. "No Security Without Time Protection: We Need a New Hardware-Software Contract." [https://ts.data61.csiro.au/publications/csiro_full_text//Ge_YH_18.pdf] | ||
* [Ge2018b] Ge, Qian et al. "Time Protection: the Missing OS Abstraction." [https://ts.data61.csiro.au/publications/papers/Ge_YCH_18_1.pdf] | * [Ge2018b] Ge, Qian et al. "Time Protection: the Missing OS Abstraction." [https://ts.data61.csiro.au/publications/papers/Ge_YCH_18_1.pdf] | ||
| + | * [seL4] The seL4 microkernel [https://ts.data61.csiro.au/projects/seL4/] | ||
==Links== | ==Links== | ||
| Line 65: | Line 74: | ||
[[Category:PULP]] | [[Category:PULP]] | ||
[[Category:FPGA]] | [[Category:FPGA]] | ||
| − | [[Category: | + | [[Category:ASIC]] |
| − | [[Category: | + | [[Category:Completed]] |
| − | [[Category: | + | [[Category:Master Thesis]] |
| + | [[Category:2020]] | ||
<!-- | <!-- | ||
Latest revision as of 18:16, 20 May 2020
Contents
Introduction
The Spectre and Meltdown vulnerabilities that publicly surfaced about a year ago did not only severely impact companies and cloud service providers, but also shook our trust in the computing systems we use on a daily basis, such as our laptops and mobile phones [masters2018]. These vulnerabilities are essentially a combination of speculative execution techniques present in today's processors, combined with shared hardware state and timing channels that make it possible to leak information.
Timing channels are among the remaining unsolved problems in secure hardware architecture design, and it is argued that security needs a new hardware-software contract [Ge2018a], [Ge2018b]. Security is and has always been the operating system's (OS) job. For instance, memory protection is already well established - but the OS must also enforce time protection. In order to enforce time protection, additional hardware support for state flushing is required.
In this project, we will investigate how such hardware knobs can be added to the Ariane 64bit RISC-V processor and come up with a proof-of-concept implementation. Insights gained during this process shall be fed back to the RISC-V community in order to guide the design of future secure RISC-V systems.
Project description
The purpose of this project is to enhance the Ariane RISC-V processor [arianeGit] with additional hardware mechanisms to flush the state of various functional and non-functional units in the pipeline. Specifically, we need to be able to erase state from
- functional units,
- instruction frontend,
- translation look-aside buffer (TLBs),
- branch predictor(s),
- instruction and data caches
in an effective way and with predictable or even constant latency [Ge2018a]. These knobs are then exposed to an OS that implements the mitigation techniques outlined in [Ge2018b].
Your task will be to carry out and test the required hardware mechanisms both in simulation and on a FPGA mapping of the Ariane processor. Further, the power, area and timing impact of the implemented mechanisms shall be assessed by mapping the core to a modern ASIC technology.
Depending on the project progress, initial experiments with the seL4 microkernel [seL4] can be carried out in collaboration with University of South Wales (UNSW).
Required Skills
To work on this project, you will need:
- to have worked in the past with at least one RTL language (SystemVerilog or Verilog or VHDL) -- having followed the VLSI1 / VLSI2 courses is mandatory
- to have prior knowledge of hardware design and computer architecture -- having followed the "Advanced System-on-Chip Design" or "Energy-Efficient Parallel Computing Systems for Data Analytics" course is recommended
Other skills that you might find useful include:
- familiarity with git, the UNIX shell, C programming
- familiarity with basic system security principles
Status: In Progress
- Supervision: Florian Zaruba, Moritz Schneider
Professors
Practical Details
Meetings & Presentations
The students and advisor(s) agree on weekly meetings to discuss all relevant decisions and decide on how to proceed. Of course, additional meetings can be organized to address urgent issues.
At the end of the project, you have to present/defend your work during a 15 min. presentation and 5 min. of discussion as part of the IIS colloquium.
Resources
- [masters2018] Jon Masters, Red Hat Inc. "Exploiting modern microarchitectures: Meltdown, Spectre, and other attacks" [2]
- [arianeGit] Ariane is a 6-stage, single issue, in-order CPU which implements the 64-bit RISC-V instruction set [3]
- [Zaruba2018] Zaruba, Florian "Ariane: An open-source 64-bit RISC-V Application-Class Processor and latest Improvements" [4]
- [data61timing] Gernot Heiser, et al. "Mitigating microarchitectural timing channels with hardware-provided operations" [5]
- [Ge2018a] Ge, Qian et al. "No Security Without Time Protection: We Need a New Hardware-Software Contract." [6]
- [Ge2018b] Ge, Qian et al. "Time Protection: the Missing OS Abstraction." [7]
- [seL4] The seL4 microkernel [8]